Google Play Protect: An upgrade to the local scanning feature based on the YARA model, the Swiss Army knife for malware researchers (and everyone else).

Google Play Protect, alongside Google Play Services and the Play Store, plays a crucial role in protecting Android devices from malware. Play Protect not only allows for security checks on apps downloaded from the Google Play Store but also enables security checks on manually installed APKs. To further enhance user security, Google may soon upgrade APK scanning with more robust rule-based local scanning, providing broader protection against malware.
Last year, Google added a feature to Play Store v37.5 for locally analyzing unknown app malware. This allows users to analyze suspicious apps without needing to upload and submit them to Google for analysis, thus making Play Protect’s threat scanning less dependent on server-side operations.
In the recently released Play Store v41.7.16, Google has upgraded its local scanning capability by integrating YARA into Play Protect. A new flag discovered in the latest version of the Play Store explicitly states, “YARA scan added for APK analysis.”
So, what exactly is YARA? YARA is a tool designed to help identify and classify malware samples, focusing more on broader malware families rather than individual pieces of malware. Traditional hash-based malware detectors search for exact hash matches, which malware can evade by altering small parts of themselves to create new hashes. YARA works by detecting common code (i.e., malware families) rather than exact hashes, using a rule-based approach to create family descriptions. This enables YARA to detect a broader spectrum of malware effectively.
Each description (also called a rule) consists of a set of strings and a boolean expression that defines its logic. Let’s look at an example:
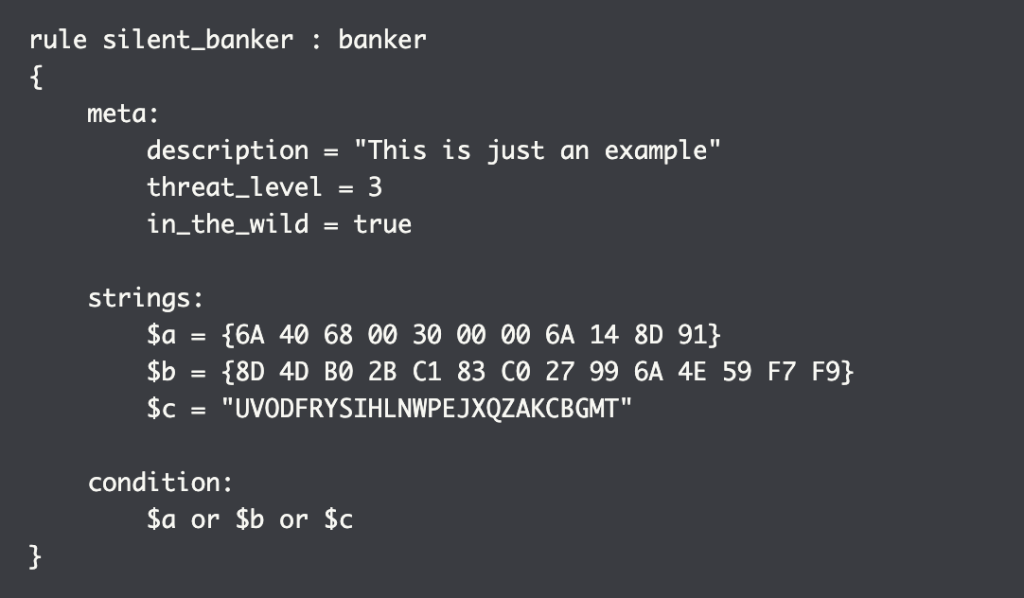
The above rule tells YARA that any file containing one of the three strings must be reported as silent_banker. This is just a simple example. More complex and powerful rules can be created using wildcards, case-insensitive strings, regular expressions, special operators, and many other features, which are described in YARA’s documentation.
YARA is multi-platform and can run on Windows, Linux, and Mac OS X. It can be used through its command-line interface or via Python scripts with the yara-python extension.
As far as we know, Google Play Protect will soon offer local scanning capabilities using the YARA model. This will be a significant upgrade to local APK scanning. While it may still not compare to cloud-based scanning, it should be sufficient for basic malware detection tasks. This improvement will greatly enhance the security of user devices, providing more peace of mind when installing applications.
Summary:
- Google Play Protect can locally scan APKs installed from outside the Google Play Store.
- This local scanning capability will soon be upgraded to use the YARA model, employing a rule-based approach to detect malware families.
- YARA should allow Play Protect to more effectively detect a broader range of malware.
- Overall, with the addition of YARA, Google Play Protect will more effectively safeguard Android devices against various malware, offering users a more secure experience.




