In recent years, major cases of Meta theft have occurred from time to time. According to the latest feedback from many Top advertisers and agenys, the amount involved in Meta fraud cases can easily reach millions of dollars.
Generally, when advertisers submit complaints about stolen cases, Meta communication will raise the issue of personal accounts being stolen or BM being stolen. In addition to these two methods, there are many gimmicky and evil ways on the market that make it difficult for everyone to guard against.
Stolen personal account
First of all, the most common of many cases of theft is the theft of FB personal accounts. After the embezzlers obtain the personal account, they can easily gain access to the assets managed by the personal account, thereby intervening in advertising and misappropriating it at will, which will bring about a chain effect of “the first number dies prematurely and causes thousands of losses” to advertisers.
Steal BM
Secondly, embezzlers often misappropriate advertisers’ BM assets by obtaining administrator rights or other black technology means. What’s more, after sneaking into BM, they eliminate many administrators of the original assets one by one. Illegal occupation of BM for a short period of time can easily result in consequences worth millions of dollars!
Examples:
(1) BM hidden administrator
Many advertisers know that there are hidden administrators in personal advertising accounts. In fact, there are also tricks in BM.
There are two main places for administrators in BM. One is our common place to check administrators, that is, Users -> Personal Users in the left navigation of BM. Another place that is likely to be ignored is User->Partners. Partners here also have management rights.
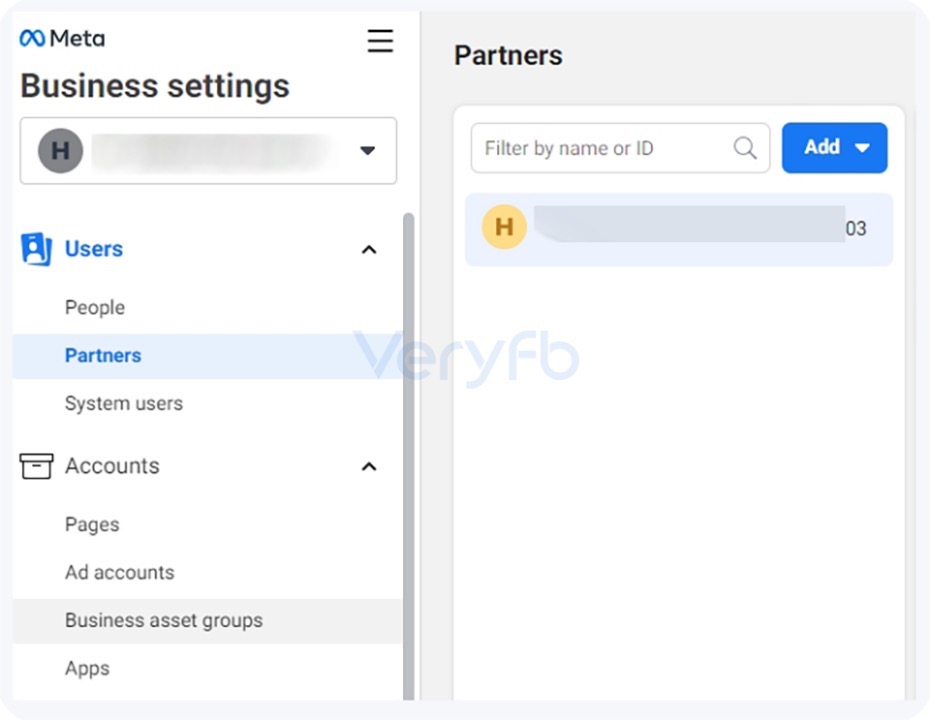
Especially advertisers whose BM assets have unknown origins are at greater risk of being stolen.
(2) Remote software intrusion
There have been reports of typical theft cases. The pirates installed remote software such as Sunflower through the advertiser’s desktop. After obtaining the remote files, they could copy any information on the computer without anyone noticing, thus making it impossible to log in to the FB account. Secondary authentication (Google’s secondary authentication) is in name only.
(3) Google account secrets leaked
Many advertisers focus on the asset itself and fail to notice that the Google account already has strange login records. In particular, some rampant hackers have implanted Trojan horse programs, and even changing passwords has little effect.




